Matter update may finally take the tedium out of setting up your smart home
There is no product category that better embodies the XKCD take on standards than smart home. With an ocean of connectivity options and incompatible standards, taming this mess has been challenging, but Matter could finally have a shot at making things a little less frustrating. The latest version of the standard has launched, offering multiple ways to streamline the usually aggravating setup process.
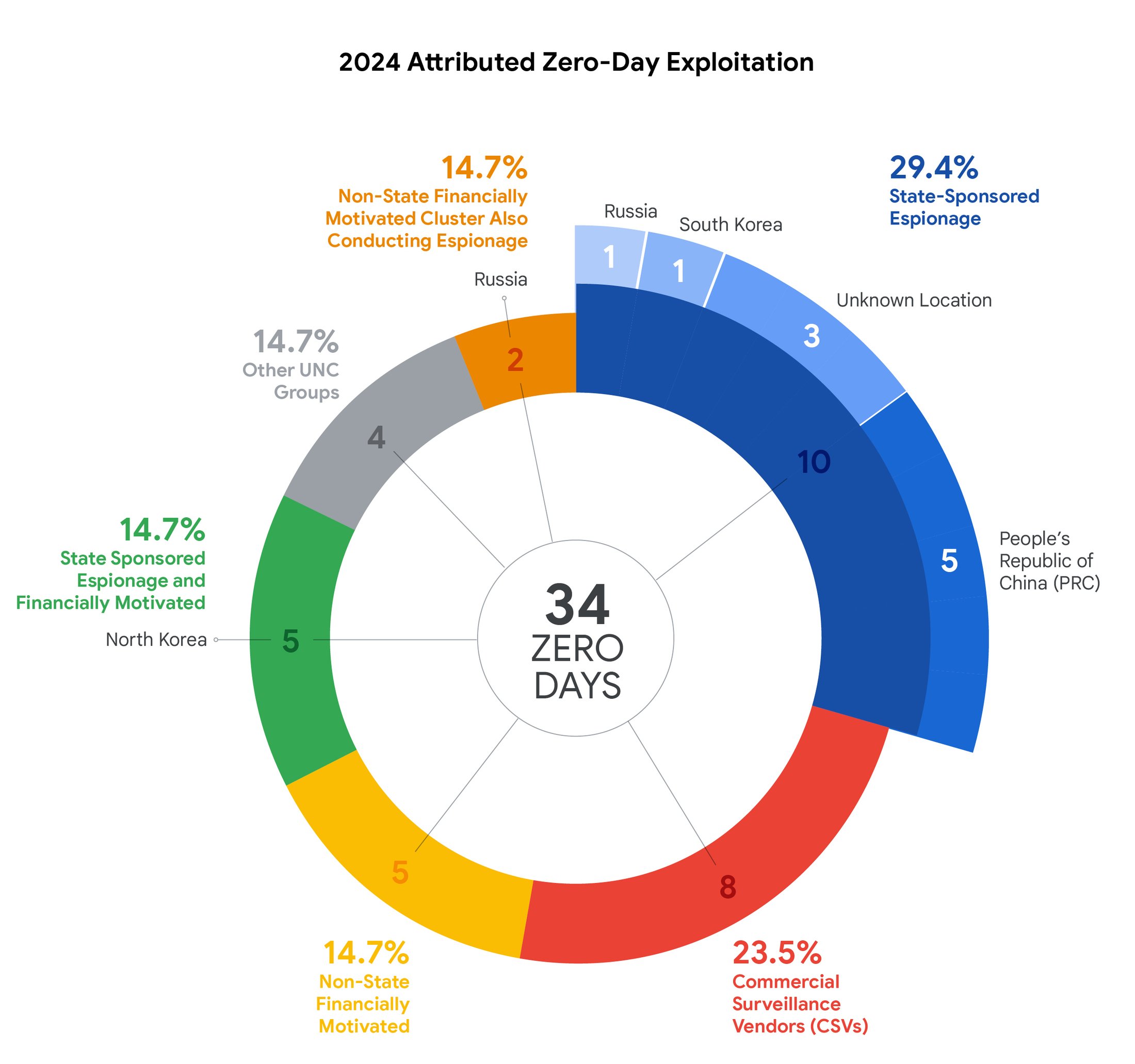
The first public release of Matter was in late 2022, but compatible systems didn’t get support until the following year. Now, there are Matter-certified devices like smart bulbs and sensors that will talk to Apple, Google, Amazon, and other smart home platforms. Matter 1.4.1 includes support for multi-device QR codes, NFC connection, and integrated terms and conditions—all of these have the potential to eliminate some very real smart home headaches.
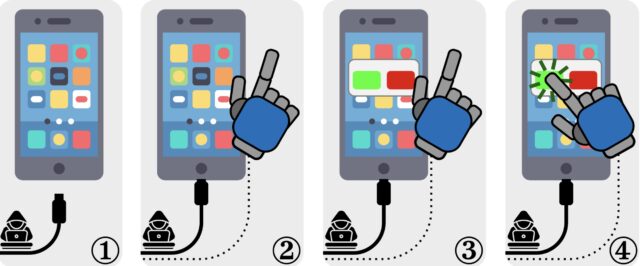
It’s common for retailers to offer multi-packs of devices like light bulbs or smart plugs. That can save you some money, but setting up all those devices is tedious. With Matter 1.4.1, it might be much easier thanks to multi-device QR codes. Manufacturers can now include a QR code in the package that will pair all the included devices with your smart home system when scanned.
QR codes will still appear on individual devices for pairing, but it might not always be a QR code going forward. The new Matter also gives manufacturers the option of embedding NFC tags inside smart home gadgets. So all you have to do to add them to your system is tap your phone. That will be nice if you need to pair a device after it has been installed somewhere that obscures the visible code.
Matter update may finally take the tedium out of setting up your smart home Read More »