Ivanti CEO pledges to “fundamentally transform” its hard-hit security model
Ivanti exploits in 2024 —
Part of the reset involves AI-powered documentation search and call routing.

Getty Images
Ivanti, the remote-access company whose remote-access products have been battered by severe exploits in recent months, has pledged a “new era,” one that “fundamentally transforms the Ivanti security operating model” backed by “a significant investment” and full board support.
CEO Jeff Abbott’s open letter promises to revamp “core engineering, security, and vulnerability management,” make all products “secure by design,” formalize cyber-defense agency partnerships, and “sharing information and learning with our customers.” Among the details is the company’s promise to improve search abilities in Ivanti’s security resources and documentation portal, “powered by AI,” and an “Interactive Voice Response system” for routing calls and alerting customers about security issues, also “AI-powered.”
Ivanti CEO Jeff Abbott addresses the company’s “broad shift” in its security model.
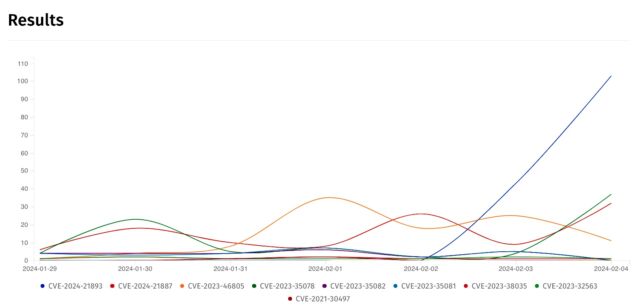
Ivanti and Abbott seem to have been working on this presentation for a while, so it’s unlikely they could have known it would arrive just days after four new vulnerabilities were disclosed for its Connect Secure and Policy Secure gateway products, two of them rated for high severity. Those vulnerabilities came two weeks after two other vulnerabilities, rated critical, with remote code execution. And those followed “a three-week spree of non-stop exploitation” in early February, one that left security directors scrambling to patch and restore services or, as federal civilian agencies did, rebuild their servers from scratch.
Because Ivanti makes VPN products that have been widely used in large organizations, including government agencies, it’s a rich target for threat actors and a target that’s seemed particularly soft in recent years. Ivanti’s Connect Secure, a VPN appliance often abbreviated as ICS, functions as a gatekeeper that allows authorized devices to connect.
Due to its wide deployment and always-on status, an ICS has been a rich target, particularly for nation-state-level actors and financially motivated intruders. ICS (formerly known as Pulse Connect) has had zero-day vulnerabilities previously exploited in 2019 and 2021. One PulseSecure vulnerability exploit led to money-changing firm Travelex working entirely from paper in early 2020 after ransomware firm REvil took advantage of the firm’s failure to patch a months-old vulnerability.
While some security professionals have given the firm credit, at times, for working hard to find and disclose new vulnerabilities, the sheer volume and cadence of vulnerabilities requiring serious countermeasures has surely stuck with some. “I don’t see how Ivanti survives as an enterprise firewall brand,” security researcher Jake Williams told the Dark Reading blog in mid-February.
Hence the open letter, the “new era,” the “broad shift,” and all the other pledges Ivanti has made. “We have already begun applying learnings from recent incidents to make immediate (emphasis Abbott’s) improvements to our own engineering and security practices. And there is more to come,” the letter states. Learnings, that is.
Ivanti CEO pledges to “fundamentally transform” its hard-hit security model Read More »