Record DDoS pummels site with once-unimaginable 7.3Tbps of junk traffic
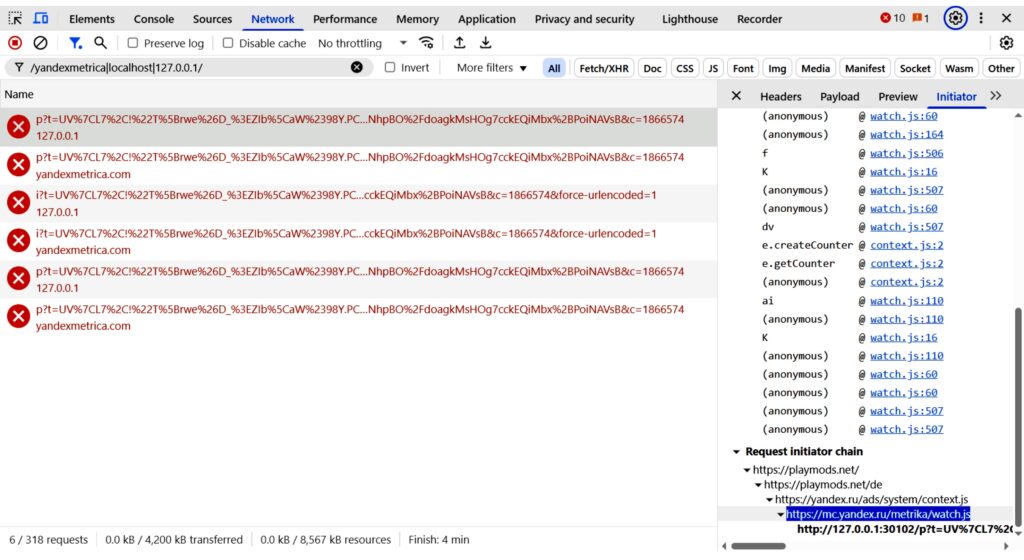
Large-scale attacks designed to bring down Internet services by sending them more traffic than they can process keep getting bigger, with the largest one yet, measured at 7.3 terabits per second, being reported Friday by Internet security and performance provider Cloudflare.
The 7.3Tbps attack amounted to 37.4 terabytes of junk traffic that hit the target in just 45 seconds. That’s an almost incomprehensible amount of data, equivalent to more than 9,300 full-length HD movies or 7,500 hours of HD streaming content in well under a minute.
Indiscriminate target bombing
Cloudflare said the attackers “carpet bombed” an average of nearly 22,000 destination ports of a single IP address belonging to the target, identified only as a Cloudflare customer. A total of 34,500 ports were targeted, indicating the thoroughness and well-engineered nature of the attack.
The vast majority of the attack was delivered in the form of User Datagram Protocol packets. Legitimate UDP-based transmissions are used in especially time-sensitive communications, such as those for video playback, gaming applications, and DNS lookups. It speeds up communications by not formally establishing a connection before data is transferred. Unlike the more common Transmission Control Protocol, UDP doesn’t wait for a connection between two computers to be established through a handshake and doesn’t check whether data is properly received by the other party. Instead, it immediately sends data from one machine to another.
UDP flood attacks send extremely high volumes of packets to random or specific ports on the target IP. Such floods can saturate the target’s Internet link or overwhelm internal resources with more packets than they can handle.
Since UDP doesn’t require a handshake, attackers can use it to flood a targeted server with torrents of traffic without first obtaining the server’s permission to begin the transmission. UDP floods typically send large numbers of datagrams to multiple ports on the target system. The target system, in turn, must send an equal number of data packets back to indicate the ports aren’t reachable. Eventually, the target system buckles under the strain, resulting in legitimate traffic being denied.
Record DDoS pummels site with once-unimaginable 7.3Tbps of junk traffic Read More »