Ransomware mastermind LockBitSupp reveled in his anonymity—now he’s been ID’d
TABLES TURNED —
The US places a $10 million bounty for the arrest of Dmitry Yuryevich Khoroshev.

Enlarge / Dmitry Yuryevich Khoroshev, aka LockBitSupp
UK National Crime Agency
Since at least 2019, a shadowy figure hiding behind several pseudonyms has publicly gloated for extorting millions of dollars from thousands of victims he and his associates had hacked. Now, for the first time, “LockBitSupp” has been unmasked by an international law enforcement team, and a $10 million bounty has been placed for his arrest.
In an indictment unsealed Tuesday, US federal prosecutors unmasked the flamboyant persona as Dmitry Yuryevich Khoroshev, a 31-year-old Russian national. Prosecutors said that during his five years at the helm of LockBit—one of the most prolific ransomware groups—Khoroshev and his subordinates have extorted $500 million from some 2,500 victims, roughly 1,800 of which were located in the US. His cut of the revenue was allegedly about $100 million.
Damage in the billions of dollars
“Beyond ransom payments and demands, LockBit attacks also severely disrupted their victims’ operations, causing lost revenue and expenses associated with incident response and recovery,” federal prosecutors wrote. “With these losses included, LockBit caused damage around the world totaling billions of US dollars. Moreover, the data Khoroshev and his LockBit affiliate co-conspirators stole—containing highly sensitive organizational and personal information—remained unsecure and compromised in perpetuity, notwithstanding Khoroshev’s and his co-conspirators’ false promises to the contrary.”
The indictment charges the Russian national with one count of conspiracy to commit fraud, extortion, and related activity in connection with computers, one count of conspiracy to commit wire fraud, eight counts of intentional damage to a protected computer, eight counts of extortion in relation to confidential information from a protected computer, and eight counts of extortion in relation to damage to a protected computer. If convicted, Khoroshev faces a maximum penalty of 185 years in prison.
In addition to the indictment, officials in the US Treasury Department—along with counterparts in the UK and Australia—announced sanctions against Khoroshev. Among other things, the US sanctions allow officials to impose civil penalties on any US person who makes or facilitates payments to the LockBit group. The US State Department also announced a $10 million reward for any information leading to Khoroshev’s arrest and or conviction.
Rooting out LockBit
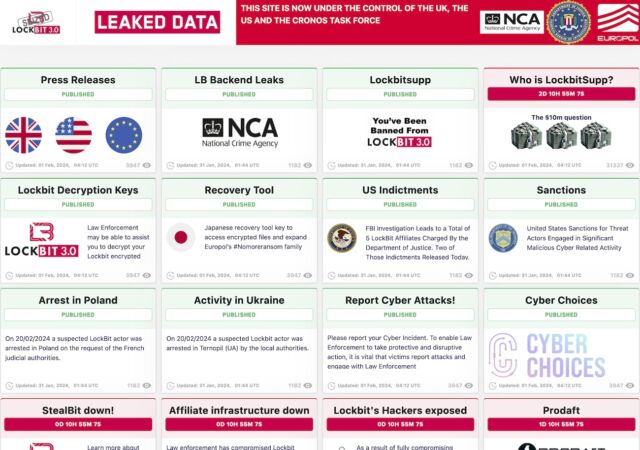
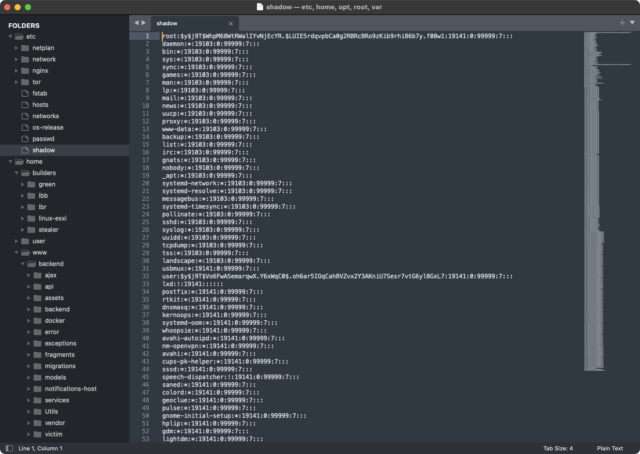
Tuesday’s actions come 11 weeks after law enforcement agencies in the US and 10 other countries struck a major blow to the infrastructure LockBit members used to operate their ransomware-as-a-service enterprise. Images federal authorities posted to the dark web site where LockBit named and shamed victims indicated they had taken control of /etc/shadow, a Linux file that stores cryptographically hashed passwords. The file, among the most security-sensitive ones in Linux, can be accessed only by a user with root, the highest level of system privileges.
In all, the authorities said in February, they seized control of 14,000 LockBit-associated accounts and 34 servers located in the Netherlands, Germany, Finland, France, Switzerland, Australia, the US, and the UK. Two LockBit suspects were arrested in Poland and Ukraine, and five indictments and three arrest warrants were issued. The authorities also froze 200 cryptocurrency accounts linked to the ransomware operation. The UK’s National Crime Agency on Tuesday said the number of active LockBit affiliates has fallen from 114 to 69 since the February action, named Operation Cronos.
In mid-March, an Ontario, Canada, man convicted on charges for working for LockBit was sentenced to four years in prison. Mikhail Vasiliev, 33 years old at the time of sentencing, was arrested in November 2022 and charged with conspiring to infect protected computers with ransomware and sending ransom demands to victims. He pleaded guilty in February to eight counts of cyber extortion, mischief, and weapons charges.
The real-world identity of Khoroshev’s LockBitSupp alter ego has been hotly sought after for years. LockBitSupp thrived on his anonymity in frequent posts to Russian-speaking hacking forums, where he boasted about the prowess and acumen of his work. At one point, he promised a $10 million reward to anyone who revealed his identity. After February’s operation taking down much of the LockBit infrastructure, prosecutors hinted that they knew who LockBitSupp was but stopped short of naming him.
LockBit has operated since at least 2019 and has also been known under the name “ABCD” in the past. Within three years of its founding, the group’s malware was the most widely circulating ransomware. Like most of its peers, LockBit has operated under what’s known as ransomware-as-a-service, in which it provides software and infrastructure to affiliates who use it to do the actual hacking. LockBit and the affiliates then divide any resulting revenue.
Story updated to correct Khoroshev’s age. Initially the State Department said his date of birth was 17 April 1973. Later, the agency said it was 17 April 1993.
Ransomware mastermind LockBitSupp reveled in his anonymity—now he’s been ID’d Read More »