I use these 2 apps for universal AirDrop rather than pushing people to Apple
Let’s clear the AirDrop —
They’re free, they’re easy, they’re open source, and they generate funny names.
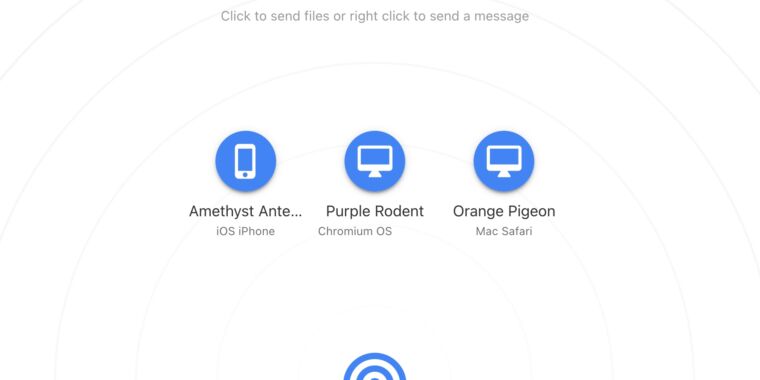
Enlarge / These kinds of sharing names are fun to shout across the house (I have first-hand knowledge of this).
Kevin Purdy
I like AirDrop just fine for sending files between devices, but I’m the only one of two humans in my household that regularly uses Apple devices. I cannot, to paraphrase the Apple CEO’s litigation-influencing quip, simply buy my spouse an iPhone. And a MacBook. And sell our household Chromebook. And give up entirely on Windows-based PC gaming.
Instead, I’ve come to use two apps to send files between operating systems on the same Wi-Fi, whether they’re systems from Cupertino, Redmond, Mountain View, or elsewhere. One is LocalSend, a cross-platform app with an open source client and protocol that I install wherever I can. The other lower-friction tool that’s especially handy for guests and rarely used devices is SnapDrop, a website or web app you open on both devices and then send files through, entirely on your local network. It, too, has its code out there for anybody to view.
Neither of these apps is new, which is good. They’ve been around long enough to garner good reviews and trust from their users. Beyond sharing files between two humans, I’ve also leaned on them when setting up headless systems or other quirky devices.
Snapdrop, for one-off transfers or quirky systems
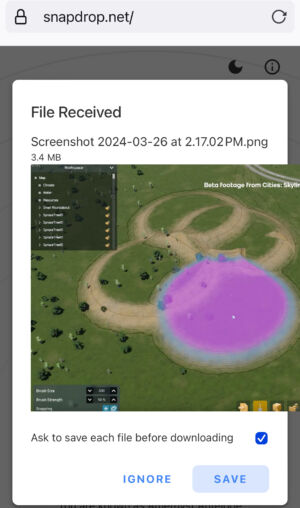
I don’t always have the patience to install the Flatpak or App Store version of LocalSend on every Raspberry Pi, Linux partition, or tablet in my house. If I need to send an image, a torrent file, or even just a long text string or web address across my home, and if both systems are technically capable of opening a browser, I use Snapdrop.
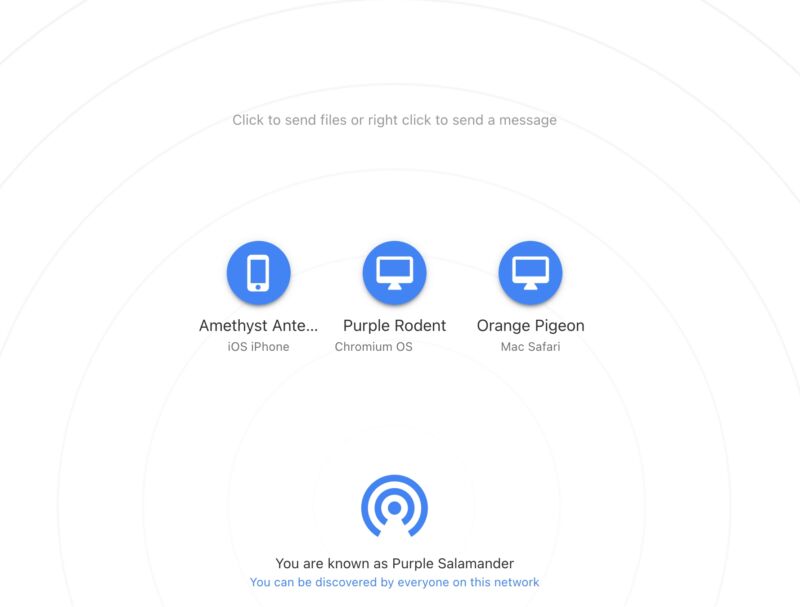
You open the browser on each device, head to Snapdrop.net, and then, almost always, you see both computers on your network. Each gets an icon and a quirky but memorable name, like “Purple Salamander” or “Green Rodent.” Click on the other computer’s icon to then pick a file and send it. Right-click (or tap-and-hold on mobile) to send a text message. There are icons in the upper-right corner if you want to install Snapdrop as a PWA (web app), switch between light and dark modes, or get links to the app’s GitHub repo or social channels.
That’s it—that’s the app. You could host your own instance on Docker if you want. And you can and should donate if you find it useful. A few key things from the FAQ:
- Snapdrop is peer-to-peer through WebRTC and only uses SnapDrop’s hosting for a Signaling Server.
- Because it’s using WebRTC, files and messages are encrypted on transit. Snapdrop doesn’t see the files; “Snapdrop doesn’t even use a database,” the author writes.
- The developer only ever intends to keep this project as a way to send files instantly over local networks and willfully rejects new feature ideas.
Once in a while, the Snapdrop site has failed to load on a device, but I’m not the kind of person who can confidently blame that on the device, local network, ISP, regional network, global DNS quirks, sunspots, or whatever else. I’m glad when it works. If it doesn’t work, I can fall back to LocalSend.
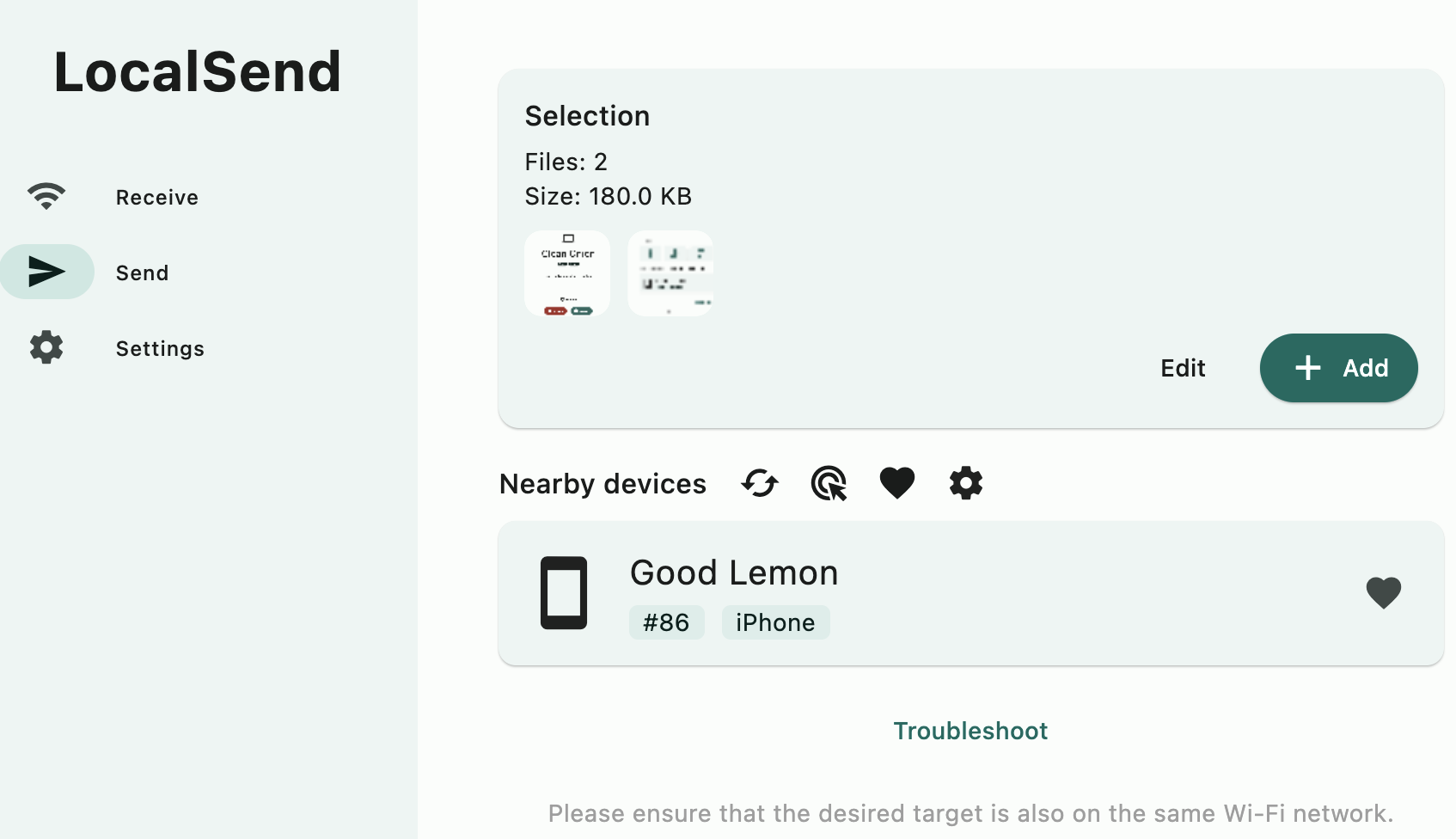
LocalSend, the belt-and-suspenders local transfer system
LocalSend is nearly as simple and focused as SnapDrop, but it doesn’t rely on the wider global web for anything and can more ably get around the occasional can’t-see-you quirks.
The client is available for just about all the major systems, usually in both app store and unofficial channels (Homebrew, Android side-loading, Flathub, etc.). You can send more kinds of things with one click than on Snapdrop, including folders and photos from a phone’s library. If a device doesn’t show up, you can manually enter its local IP address to find it (which has worked for me a few times). You can favorite a device, send to multiple devices, send multiple files, send via link, choose to have files automatically accepted and saved to a folder of your choice, and otherwise set up things to your liking. And because it’s a locally installed app, you can send files to it through your system’s share/send dialogues.
LocalSend says it relies on HTTPS connections and a REST API to send between devices, with a TLS/SSL certificate generated on the fly on each device. As with Snapdrop, you can compile and run LocalSend yourself.
I’ll welcome any other suggestions for same-network file sharing in the comments. Both of these apps save me from having to log into web-based file-sharing systems every time I just want to show a funny photo or share a PDF, and for that, I thank them.
I use these 2 apps for universal AirDrop rather than pushing people to Apple Read More »