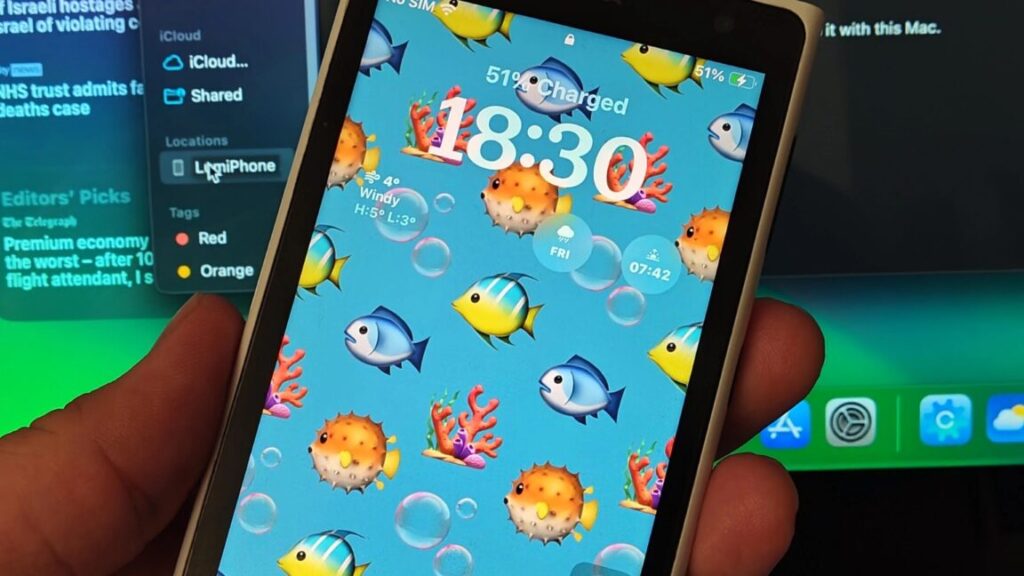
“NokiApple LumiPhone 1020 SE” merges Windows Phone body with budget iPhone guts
Remember the Lumia 1020? It’s back—in iPhone SE form.
The Lumia 1020 was a lot of smartphone in July 2013. It debuted with a focus “almost entirely on the phone’s massive camera,” Ars wrote at the time. That big 41-megapixel sensor jutted forth from the phone body, and Nokia reps showed off its low-light, rapid-motion camera abilities by shooting pictures of breakdancers in a dark demonstration room. The company also offered an optional camera grip—one that made it feel a lot more like a point-and-shoot camera. In a more robust review, Ars suggested the Lumia 1020 might actually make the point-and-shoot obsolete.
Front of the Lumia 1020, showing a bit of Windows Phone square grid flair. Casey Johnston
The Lumia 1020 contained yet another cutting edge concept of the day: Windows Phone, Microsoft’s color-coded, square-shaped companion to its mobile-forward Windows 8. The mobile OS never got over the users/apps, chicken/egg conundrum, and called it quits in October 2017. The end of that distant-third-place mobile OS would normally signal the end of the Lumia 1020 as a usable phone.
But there was a person named /u/OceanDepth95028 who saw beyond, and where others thought, “LOL,” this person thought, “Why not?” And this person looked at the Lumia 1020 and saw a third-generation iPhone SE inside of it. And then this person made that phone, and it booted. And the person saw that it was good, and they posted the tale to Reddit’s r/hackintosh.
“NokiApple LumiPhone 1020 SE” merges Windows Phone body with budget iPhone guts Read More »