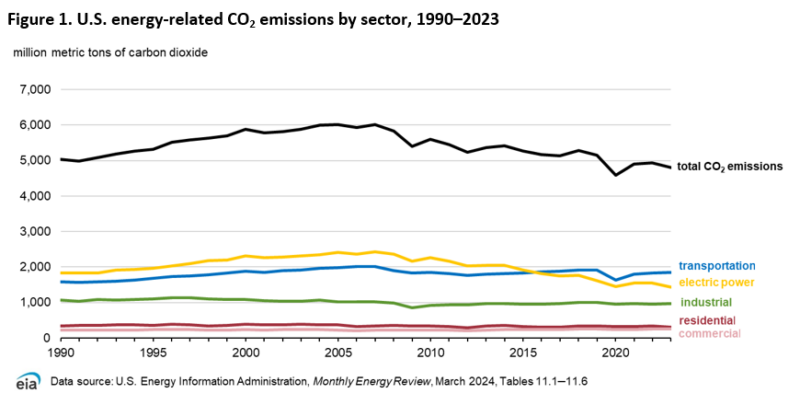
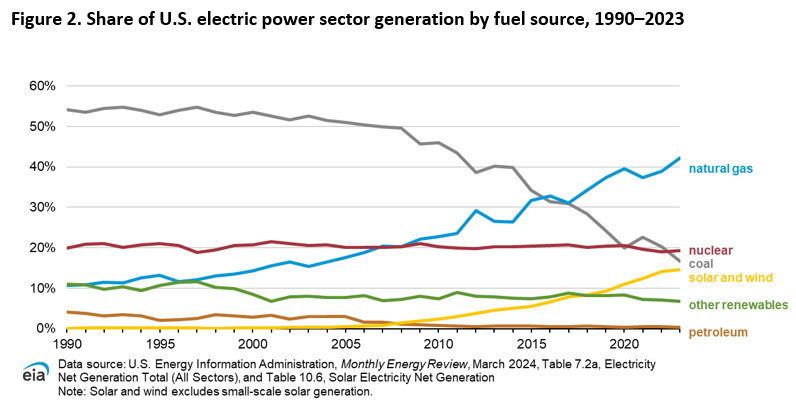
NASA still doesn’t understand root cause of Orion heat shield issue
Flight rationale —
“When we stitch it all together, we’ll either have flight rationale or we won’t.”

Enlarge / NASA’s Orion spacecraft descends toward the Pacific Ocean on December 11, 2021, at the end of the Artemis I mission.
NASA
NASA officials declared the Artemis I mission successful in late 2021, and it’s hard to argue with that assessment. The Space Launch System rocket and Orion spacecraft performed nearly flawlessly on an unpiloted flight that took it around the Moon and back to Earth, setting the stage for the Artemis II, the program’s first crew mission.
But one of the things engineers saw on Artemis I that didn’t quite match expectations was an issue with the Orion spacecraft’s heat shield. As the capsule streaked back into Earth’s atmosphere at the end of the mission, the heat shield ablated, or burned off, in a different manner than predicted by computer models.
More of the charred material than expected came off the heat shield during the Artemis I reentry, and the way it came off was somewhat uneven, NASA officials said. Orion’s heat shield is made of a material called Avcoat, which is designed to burn off as the spacecraft plunges into the atmosphere at 25,000 mph (40,000 km per hour). Coming back from the Moon, Orion encountered temperatures up to 5,000° Fahrenheit (2,760° Celsius), hotter than a spacecraft sees when it reenters the atmosphere from low-Earth orbit.
Despite heat shield issue, the Orion spacecraft safely splashed down in the Pacific Ocean. Engineers discovered the uneven charring during post-flight inspections.
No answers yet
Amit Kshatriya, who oversees development for the Artemis missions in NASA’s exploration division, said Friday that the agency is still looking for the root cause of the heat shield issue. Managers want to be sure they understand the cause before proceeding with Artemis II, which will send astronauts Reid Wiseman, Victor Glover, Christina Koch, and Jeremy Hansen on a 10-day flight around the far side of the Moon.
This will be the first time humans fly near the Moon since the last Apollo mission in 1972. In January, NASA announced a delay in the launch of Artemis II from late 2024 until September 2025, largely due to the unresolved investigation into the heat shield issue.
“We are still in the middle of our investigation on the performance of the heat shield from Artemis I,” Kshatriya said Friday in a meeting with a committee of the NASA Advisory Council.
Engineers have performed sub-scale heat shield tests in wind tunnels and arc jet facilities to better understand what led to the uneven charring on Artemis I. “We’re getting close to the final answer in terms of that cause,” Kshatriya said.
NASA officials previously said it is unlikely they will need to make changes to the heat shield already installed on the Orion spacecraft for Artemis II, but haven’t ruled it out. A redesign or modifications to the Orion heat shield on Artemis II would probably delay the mission by at least a year.
Instead, engineers are analyzing all of the possible trajectories the Orion spacecraft could fly when it reenters the atmosphere at the end of the Artemis II mission. On Artemis I, Orion flew a skip reentry profile, where it dipped into the atmosphere, skipped back into space, and then made a final descent into the atmosphere, sort of like a rock skipping across a pond. This profile allows Orion to make more precise splashdowns near recovery teams in the Pacific Ocean and reduces g-forces on the spacecraft and the crew riding inside. It also splits up the heat load on the spacecraft into two phases.
The Apollo missions flew a direct reentry profile. There is also a reentry mode available called a ballistic entry, in which the spacecraft would fly through the atmosphere unguided.

Enlarge / Ground teams at NASA’s Kennedy Space Center in Florida moved the Orion spacecraft for the Artemis II mission into an altitude chamber earlier this month.
The charred material began flying off the heat shield in the first phase of the skip reentry. Engineers are looking at how the skip reentry profile affected the performance of the Orion heat shield. NASA wants to understand how the Orion heat shield would perform during each of the possible reentry trajectories for Artemis II.
“What we have the analysis teams off doing is saying, ‘OK, independent of what the constraints are going to be, what can we tolerate?” Kshatriya said.
Once officials understand the cause of the heat shield charring, engineers will determine what kind of trajectory Artemis II needs to fly on reentry to minimize risk to the crew. Then, managers will look at building what NASA calls flight rationale. Essentially, this is a process of convincing themselves the spacecraft is safe to fly.
“When we stitch it all together, we’ll either have flight rationale or we won’t,” Kshatriya said.
Assuming NASA approves the flight rationale for Artemis II, there will be additional discussions about how to ensure Orion heat shields are safe to fly on downstream Artemis missions, which will have higher-speed reentry profiles as astronauts return from landings on the Moon.
In the meantime, preparations on the Orion spacecraft for Artemis II continue at NASA’s Kennedy Space Center. The crew and service modules for Artemis II were mated together earlier this year, and the entire Orion spacecraft is now inside a vacuum chamber for environmental testing.
NASA still doesn’t understand root cause of Orion heat shield issue Read More »